In the digital transformation era, organizations are capitalizing on Big Data and Artificial Intelligence (AI) to extract valuable insights, drive informed decisions, and maintain a competitive edge. As these technologies become indispensable to business operations, ensuring data security and AI pipelines in the cloud takes centre stage. Let’s explore the “Rings of Security” framework as a comprehensive solution to fortify Big Data and AI pipelines in the cloud. In the pursuit of leveraging vast datasets for actionable insights, organizations are increasingly migrating their Big Data pipelines to the cloud, benefiting from rapid cluster deployment, scalability, and a streamlined user experience. However, with these advantages comes the critical imperative of addressing security concerns.
Understanding Big Data and AI Pipelines
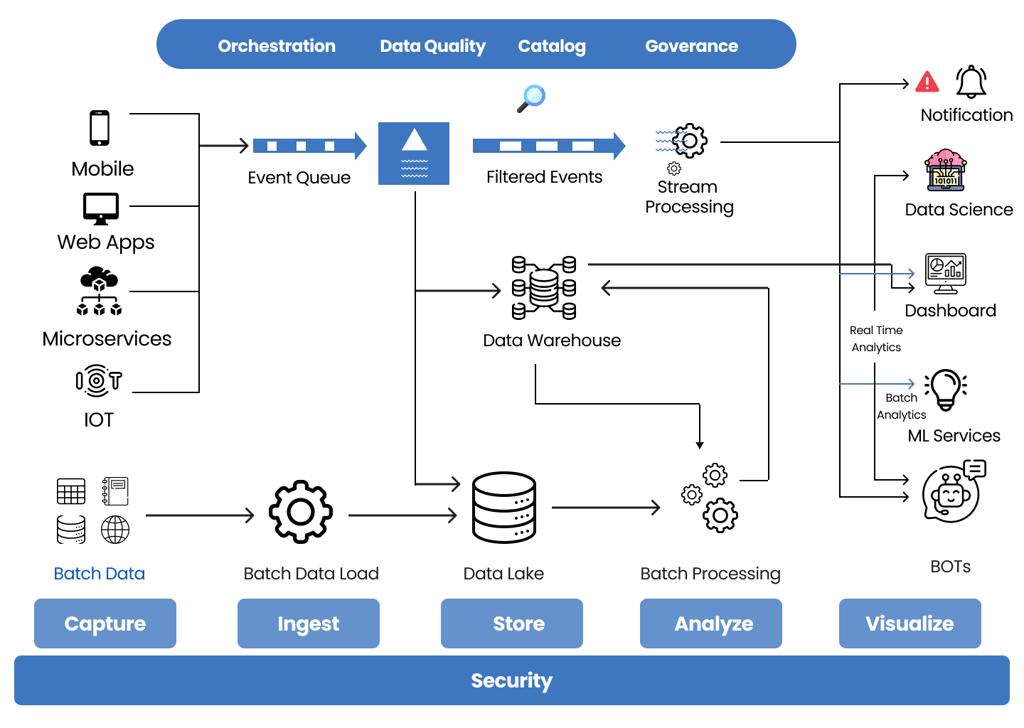
The Five Stages In the complex ballet of data processing, the Big Data and AI pipeline gracefully pirouettes through five distinct stages:
- Capture: In this initial stage, data is sourced from diverse internal and external instruments such as mobile apps, websites, and IoT devices. This phase orchestrates a harmonious stream, setting the foundation for subsequent data processing.
- Ingest: The second stage involves the graceful data entry into the pipeline through batch jobs or streams. This is akin to a choreographed dance where information unfolds in real time, contributing to the dynamic flow of the data pipeline.
- Store: As the performance progresses, raw data takes centre stage in a data lake or warehouse. Here, the data undergoes meticulous transformations, shedding its natural form and preparing for a grand performance in the later stages of the pipeline.
- Analyze: Stepping into the limelight, the analytics, data science, and machine learning components converge in a captivating performance. This stage is where the true essence of the data is extracted, unravelling insights and revelations that contribute to the narrative.
- Visualize: The grand finale of the pipeline sees the insights cascading into various forms of presentation – dashboards, emails, SMS, push notifications, and microservices. This visual spectacle ensures that the audience, whether analysts or decision-makers, can grasp the beauty of data-driven revelations.

Common Components and Threats
Amidst the diverse array of open-source components that form the orchestra of the big data and AI pipeline, there is a symphony of possibilities. However, common threats lurk in the wings of this intricate performance, disrupting the artistic rendition. The channel faces various challenges, from the orchestrated disruptions of DDoS attacks to the stealthy interludes of data theft. These challenges emphasize the need for a robust defence mechanism to safeguard the integrity and flow of data within the pipeline. Understanding the intricacies of these components and threats is essential for orchestrating an effective security strategy in big data and AI.
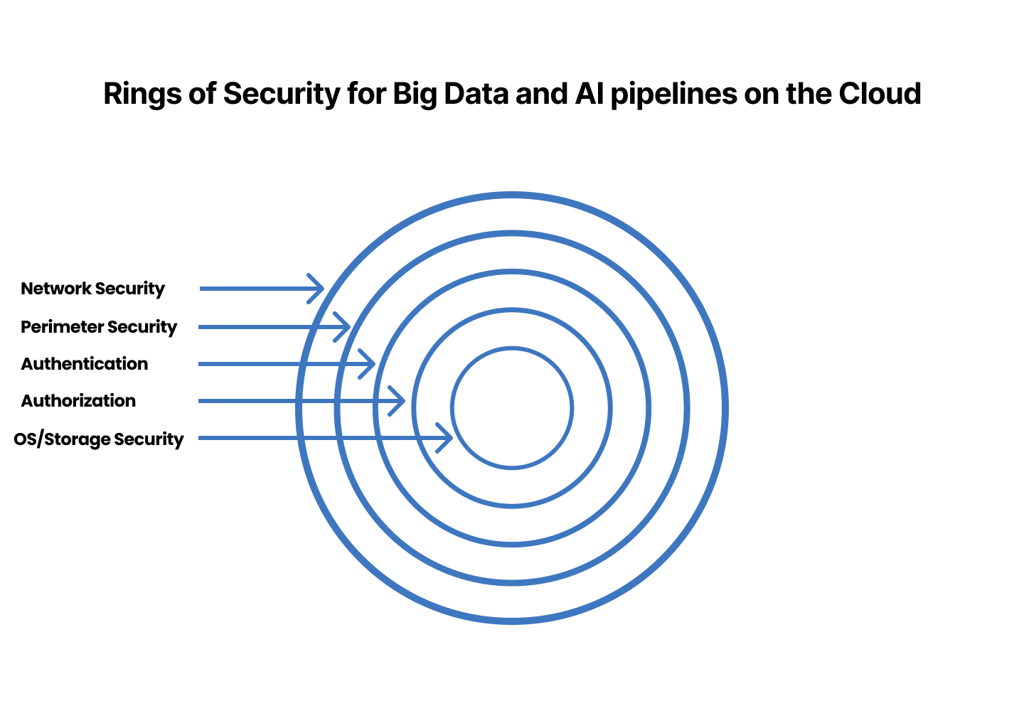
Overview of the Rings of Security Framework
The Rings of Security framework is a comprehensive strategy to fortify the cloud’s big data and AI pipelines. It entails a multi-layered defence approach to safeguard against evolving cyber threats, ensuring valuable data security, integrity, and confidentiality.
OS/Storage Security
Data encryption forms the outermost ring, the primary barrier against unauthorized access. It involves implementing robust encryption mechanisms for both transit data and rest data. This ensures that sensitive information remains classified and secure, even if intercepted.
Authentication
This ring focuses on securing the perimeter of the Big Data and AI infrastructure. It involves implementing stringent access controls, multi-factor authentication, and continuous monitoring of user activities. Only authorized personnel can access, modify, or interact with the data and analytics pipelines by fortifying the frame.
Perimeter Security
Perimeter security is a core component within the framework, addressing the secure transmission of data between different parts of the Big Data and AI ecosystem. This involves employing firewalls, intrusion detection systems, and secure communication protocols to prevent unauthorized entities from intercepting or manipulating data flow.
Authorization
The inner ring focuses on data governance and compliance. It involves establishing data handling, retention, and disposal policies and ensuring adherence to industry regulations and best practices. Regular audits and monitoring contribute to maintaining a secure and compliant environment.
Network Security
The innermost ring emphasizes real-time monitoring and anomaly detection. Organizations can use AI-driven analytics to detect abnormal patterns or activities within their big data and AI pipelines. Prompt identification of potential security threats allows for swift responses and mitigation strategies, minimizing the impact of security incidents.
Challenges and Solutions in Implementing a Robust Security Framework
Challenges
- Complex Ecosystem and Rapidly Evolving Threats: The inherent complexity of Big Data and AI ecosystems, coupled with the rapid evolution of cyber threats, poses significant challenges to implementing a robust security framework. The intricate nature of these environments requires tailored solutions to keep pace with emerging security risks.
- Data Sensitivity, Scalability, and Privacy Concerns: Managing data sensitivity, addressing scalability issues, and ensuring privacy compliance have become formidable challenges. Dealing with diverse data types and sources requires a careful balance between securing information and accommodating the expanding infrastructure’s scalability needs.
Solutions
- Holistic Risk Assessment and Adaptive Security Measures: Initiate a comprehensive chance assessment to identify vulnerabilities and prioritize security measures. Implement continuous monitoring and adaptive security strategies, utilizing AI-driven analytics to respond proactively to evolving threats. This ensures a dynamic defence mechanism against potential risks.
- Encryption, Cloud-Native Security, and Compliance Adherence: robust encryption and tokenization techniques to secure sensitive data in transit and at rest. Leverage cloud-native security solutions cloud service providers provide, addressing scalability concerns and aligning with the specific cloud platform. Adhere to industry-specific compliance frameworks and best practices to establish a structured and legally compliant approach to data security.
- Continuous Collaboration and Training: Foster collaboration among security teams, data scientists, and IT professionals. Conduct regular training programs and awareness campaigns to empower personnel with the knowledge and skills to adhere to security protocols. Human-related security lapses can be minimized through a culture of awareness and collective responsibility.
Benefits of the Rings of Security Framework
A. Tangible Benefits of Adopting the Comprehensive Security Approach
- Robust Protection Across Multiple Fronts: The Rings of Security framework offers a multi-layered defence strategy, providing organizations with comprehensive protection across various facets of their Big Data and AI pipelines. This approach ensures that potential vulnerabilities are addressed at different levels, reducing the overall risk of security breaches.
- Proactive Defense Against Evolving Threats: By incorporating elements like continuous monitoring and adaptive security measures, the framework enables organizations to adopt a proactive stance against rapidly evolving cyber threats. This mitigates the risk of potential breaches and allows for swift responses to emerging security challenges.
- Improved Incident Response and Mitigation: The structured nature of the Rings of Security facilitates efficient incident response and mitigation strategies. With monitoring and anomaly detection at its core, organizations can quickly identify and address security incidents, minimizing the impact on data integrity and operational continuity.
B. Enhancement of Data Integrity, Compliance, and Resilience
- Strengthened Data Integrity: The framework significantly contributes to maintaining data integrity by implementing encryption, access control, and monitoring measures. This ensures that the data remains unaltered and trustworthy throughout its lifecycle, enhancing the reliability of insights derived from Big Data and AI analyses.
- Adherence to Regulatory Compliance: Compliance with industry regulations and data safety laws is critical to the Rings of Security framework. By integrating data governance, compliance checks, and encryption, organizations can establish and maintain adherence to regulatory standards. This is crucial for industries with stringent data protection requirements, such as healthcare or finance.
- Overall Resilience Against Cyber Threats: The holistic nature of the Rings of Security framework contributes to the overall resilience of Big Data and AI pipelines against cyber threats. With layers dedicated to network security, access control, and anomaly detection, the organization is better equipped to withstand and recover from potential security incidents, ensuring continuous operation and minimal disruption.
Conclusion
Securing cloud-based data and AI pipelines is imperative in the dynamic landscape of digital transformation, where the fusion of big data and artificial intelligence (AI) is pivotal for organizational success. This blog navigated the intricate stages of big data and AI pipelines, unravelling complexities from capturing data to insightful visualizations. Addressing common threats, it delved into the “Rings of Security” framework, showcasing a robust defence with data encryption, access control, network security, governance, compliance, and vigilant monitoring. Challenges like a complex ecosystem and evolving threats were met with holistic risk assessment, encryption, and collaboration. The benefits unveiled include multi-layered defence, proactive threat mitigation, and enhanced data integrity, compliance, and resilience against cyber threats. In the digital transformation symphony, the Rings of Security Guard ensure organizations dance fearlessly in Big Data and AI.
VE3 is a global technology leader, providing avant-garde digital solutions that empower businesses to reach their pinnacle. With a focus on overcoming technology challenges, our expertise lies in cutting-edge domains such as digital transformation, cloud computing, blockchain, DevOps, and AI. Leveraging years of experience, we navigate the intricate landscape of enterprise platforms, ensuring a secure and resilient environment for big data and AI pipelines. Our commitment to innovation and a suite of services that align with the Rings of Security framework position VE3 as a trusted partner in securing and fortifying the digital future. To know more, explore our innovative digital solutions or contact us directly.