At Oracle, primary focus is on crafting top-notch security measures for every Software as a Service (SaaS) solution and service within the Oracle Cloud Infrastructure (OCI) framework. Simultaneously, we emphasize the significance of comprehending and assuming responsibility for distinct ownership domains across diverse cloud application deployment models, as explicated in the Oracle shared responsibility security model technical document.
It is imperative for organizations to delineate clear-cut policies and procedures governing their obligations regarding cloud security. This entails defining ownership boundaries, articulating specific security responsibilities, and instituting controls to ensure alignment with these policies. By actively engaging in the shared responsibility model, organizations can effectively mitigate security risks and uphold a secure cloud environment conducive to their operations.
Understanding the Shared Responsibility Security Model in Cloud Deployments
In the realm of cloud software-as-a-service (SaaS), the security model operates on a shared basis, in contrast to traditional on-premises application deployments. Within this framework, organizations bear specific responsibilities in a cloud application deployment, and they can adopt various best practices to fulfil these duties. These practices are outlined in detail in the accompanying figure.
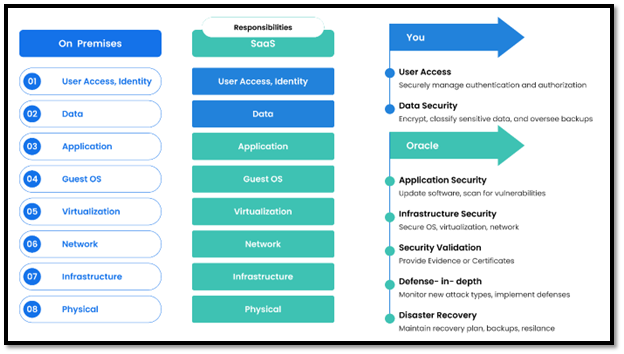
Figure 1: Illustrating the Shared Security Responsibility Model in Cloud Environments
Differentiating Customer and Oracle Roles in Cloud Security Management Across Deployment Scenarios
Let’s discuss common best practices for customer policies and procedures, offering specific examples and actionable choices for implementation within the Oracle Fusion SaaS environment.
Who Can Develop Adapters?
We advise Oracle Fusion customers to adopt a password rotation policy as part of their ongoing security practices. Administrators have the capability to establish this policy within the Oracle Fusion application, setting a requirement for administrative passwords to be changed every 90 days. This can be configured through the security settings, enabling administrators to define the password expiration period. Once configured, the system will automatically prompt administrators to update their passwords as they approach expiration.
It is essential for administrators to generate strong, unique passwords each time they rotate them to maximize the effectiveness of this security measure. By consistently rotating administrative passwords, organizations can bolster their defences against unauthorized access and potential compromise.
Multifactor authentication (MFA)
Multifactor authentication (MFA) is a security method that verifies a user’s identity by requiring more than one login credential. Alongside a password, it may involve additional verification steps such as confirmation to a mobile device or a code sent to their email. We strongly advocate for the adoption of multifactor authentication across all user and administrator accounts within cloud-based environments.
To implement MFA for Oracle Fusion applications, administrators need to establish a new Identity and Access Management (IAM) domain and federate it with Fusion. This IAM domain ensures MFA enforcement for all or specific users of Fusion applications. Many organizations opt to integrate third-party IAM solutions that offer similar MFA functionalities, enforcement mechanisms, and logging capabilities.
Enhancing Security: Identity and Application Logging Practices
As depicted in Figure 1, a key area of responsibility involves managing identity and data controls. It is essential to configure robust authentication mechanisms, including Multi-Factor Authentication (MFA), and to ensure the collection and retention of all identity and application access logs. Within the Oracle SaaS infrastructure, security logs are gathered and monitored by the Oracle SaaS Cloud Security (SCS) organization as part of the Automated SaaS Cloud Security Services (ASCSS) infrastructure. These logs are then stored in a Security Information and Event Management (SIEM) system.
However, the responsibility for managing identity and application logs lies with the customer. We recommend that organizations gather, retain, and monitor these logs within their own systems and tools. It’s also advisable to collect logs at regular intervals, as the availability, retention, and storage capabilities may vary across different applications and services. Each application relies on specific APIs and available tools for extracting audits, as most logs are not directly accessible or equipped with automated connectors.
Implementing Location-Based Access Controls for Enhanced Security
Many organizations contend with employees and users accessing the Oracle Fusion Human Capital Management (HCM) application from diverse locations and devices. In certain scenarios, these users may hold privileged roles and entitlements, exposing them to heightened risks when accessing Fusion HCM from untrusted networks. One highly recommended best practice involves enabling and configuring location-based access control (LBAC) to limit access or revoke entitlements for certain roles from less-trusted locations.
Oracle LBAC presents a feature empowering administrators to restrict access to Fusion Applications and their REST APIs based on users’ IP addresses. For those utilizing their own applications and leveraging Oracle Fusion APIs, a specific configuration is advised to ensure the most stringent access control based on location and operational requirements.
Risk management service
The Oracle Risk Management service is a cloud-based solution designed to assist organizations in effectively managing risks and ensuring compliance with regulations pertinent to their Oracle enterprise resource planning (ERP) applications. This comprehensive platform enables users to automate the analysis, monitoring, and regulation of ERP security, configurations, and transactions through the utilization of advanced data science and artificial intelligence (AI) techniques.
The service offers a library of prebuilt controls, alongside a workbench for creating customized controls, facilitating streamlined compliance assessments and audits. With Fusion Risk Management, customers gain access to a modern system of internal controls that continuously scrutinizes user access and activity data, aligning with best practices for security and compliance purposes.
Conclusion
Ensuring robust security measures and compliance with regulations is paramount for organizations deploying Oracle Fusion applications. Through the implementation of best practices such as password rotation, multifactor authentication (MFA), identity and application logging, location-based access controls (LBAC), and leveraging Oracle Risk Management services, organizations can bolster their defenses against potential threats and mitigate risks effectively. By understanding the shared responsibility model in cloud deployments and actively engaging in the management of identity, data controls, and security measures, organizations can create a secure cloud environment conducive to their operations. It’s essential for organizations to stay proactive in managing risks, continuously monitoring access, and adapting security measures to evolving threats and regulatory requirements. With the comprehensive tools and services offered by Oracle, organizations can navigate the complexities of cloud security and compliance with confidence, safeguarding their valuable data and ensuring the integrity and reliability of their Oracle Fusion applications.
Here’s where VE3 can help, we can bolster Oracle Fusion deployments by providing specialized expertise in security assessments, tailored solutions, and compliance strategies. Leveraging our knowledge, you can enhance your security posture, mitigate risks effectively, and navigate evolving regulatory requirements with confidence. To know more, explore our innovative digital solutions or contact us directly.